Description
Fortinet FortiAnalyzer VM Jeddah
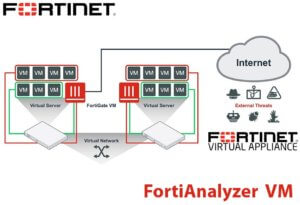
FortiAnalyzer-VM provides organizations of any size with centralized security event analysis, forensic research, reporting, content archiving, data mining, malicious file quarantining and vulnerability assessment. Centralized collection, correlation, and analysis of geographically and chronologically diverse security data from Fortinet appliances and third-party devices deliver a simplified, consolidated view of your security posture. FortiAnalyzer-VM integrates network logging, analysis, and reporting into a single system, delivering increased knowledge of security events throughout a network. Utilizing virtualization technology, FortiAnalyzer-VM is a software-based version of the FortiAnalyzer hardware appliance and is designed to run on VMware™ virtualization platforms. It offers all the features of the FortiAnalyzer hardware appliance.
Fortianalyzer Vm Jeddah
Virtualized infrastructure continues to transform today’s IT landscape. From Virtual LANs to servers and user desktops, the IT environment as a whole is increasingly becoming part of a virtualized cloud. The virtual appliance offers all of the features of our traditional hardware-based FortiAnalyzer appliances in a form factor that leverages your existing investment in virtualization technology.FortiAnalyzer-VM delivers complete security oversight with granular graphical reporting. Its breadth of data collection functions eliminate blind spots in understanding your security posture. Its unique forensic analysis tools provide you with the ability to discover, analyze, and mitigate threats before perimeter breach or data loss/ theft occurs. The FortiAnalyzer-VM’s forensic analysis tool enables detailed user activity reports, while the vulnerability assessment tool automatically discovers, inventories and assesses the security posture of servers and hosts within the network infrastructure.
The FortiAnalyzer virtual appliance family minimizes the effort required to monitor and maintain acceptable use policies, as well as identify attack patterns that can be used to fine tune the security policy, thwarting future attackers. In addition, FortiAnalyzer-VM provides detailed data capture that can be used for forensic purposes to comply with regulations and policies regarding privacy and disclosure of information security breaches.
Fortinet FortiAnalyzer VM Features
- Over 550 reports and customizable charts help monitor and maintain identify attack patterns, acceptable use policies, and demonstrate policy compliance
- Network capacity and utilization data reporting allow you to plan and manage networks more efficiently
- Scalable architecture allows the device to run in collector or analyzer modes for optimized log processing
- Advanced features such as event correlation, forensic analysis, and vulnerability assessment provide essential tools for in-depth protection of complex networks
- Secure data aggregation from multiple FortiGate and FortiMail™ security appliances provides network-wide visibility and compliance
Enhanced Visibility With FortiAnalyzer Platforms
FortiAnalyzer platforms integrate network logging, analysis, and reporting into a single system, delivering increased knowledge of security events throughout your network. They provide organizations of any size with centralized security event analysis, forensic research, reporting, content archiving, data mining, malicious file quarantining and vulnerability management. Centralized collection, correlation, and analysis of geographically and chronologically diverse security data from Fortinet appliances and third-party devices deliver a simplified, consolidated view of your security posture.
The FortiAnalyzer family minimizes the effort required to monitor and maintain acceptable use policies, as well as identify attack patterns to help you fine tune your policies. In addition, FortiAnalyzer platforms provide detailed data capture for forensic purposes to comply with policies regarding privacy and disclosure of information security breaches.
Security Event Information Management
You can put time back in your day by deploying a FortiAnalyzer platform into your security infrastructure, creating a single view of your security events, archived content, and vulnerability assessments. FortiAnalyzer platforms accept a full range of data from Fortinet solutions, including traffic, event, virus, attack, content filtering, and email filtering data. It eliminates the need to manually search multiple log files or manually analyze multiple consoles when performing forensic analysis or network auditing. A FortiAnalyzer platform’s central data archiving, file quarantine and vulnerability assessment further reduce the amount of time you need to spend managing the range
Choice of Form Factor
Very few organizations use 100% hardware IT infrastructure or 100% virtual IT infrastructure today, creating a need for both hardware appliances and virtual appliances in your security strategy. FortiAnalyzer can be deployed as either hardware or a virtual appliance to fit your environment, which may include a mix of virtual and physical IT infrastructure. FortiAnalyzer will log events from FortiOS-based hardware appliances, virtual appliances, or a combination of both.